
Threat Modeling Gameplay with EoP
Coming soon to a bookshelf near you, Threat Modeling Gameplay with EoP: A reference manual for spotting threats in software architecture

Coming soon to a bookshelf near you, Threat Modeling Gameplay with EoP: A reference manual for spotting threats in software architecture

Some interesting security and creativity games plus a few more
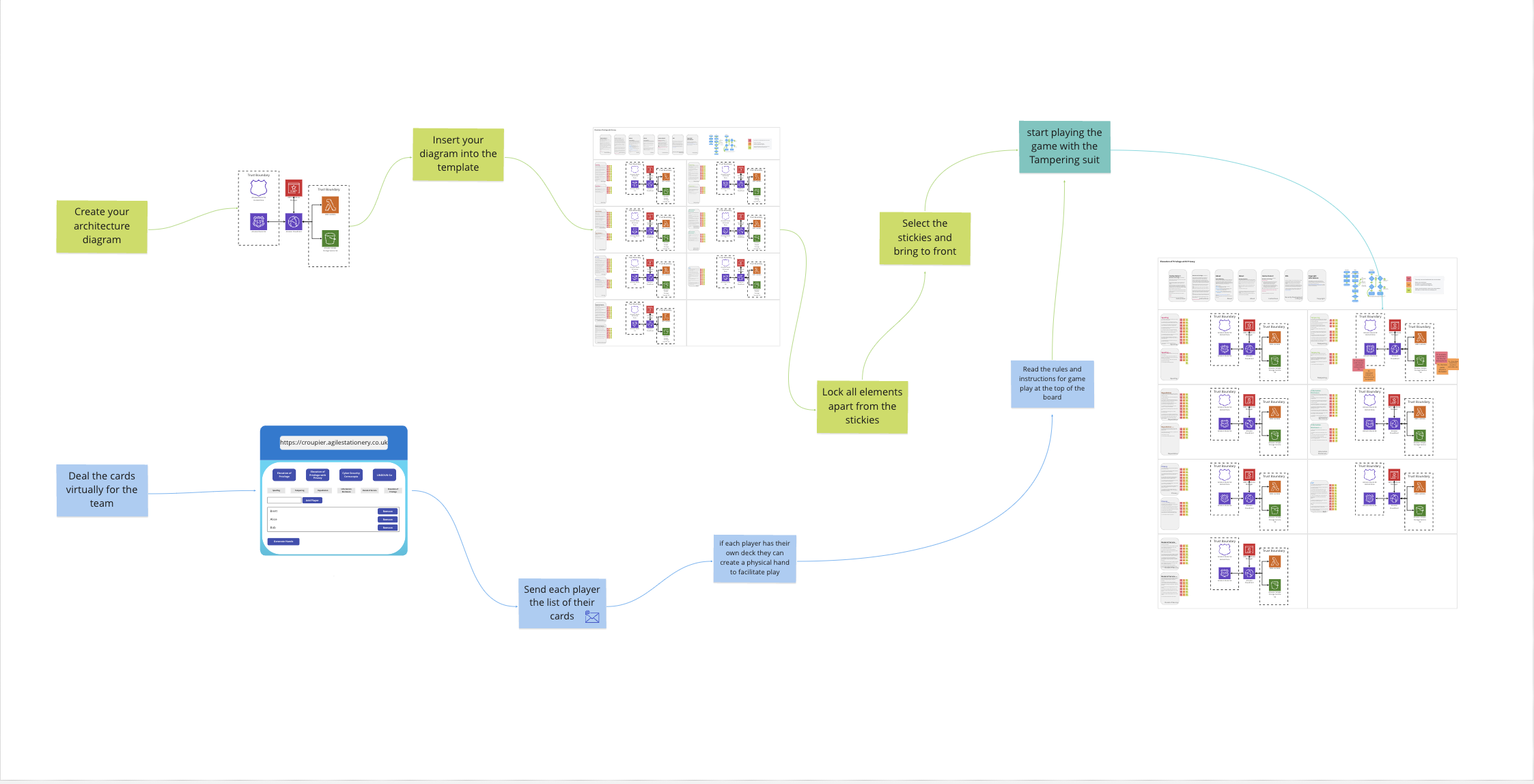
Threat modeling with teams is a process that requires visuals, interaction between team members and discussion and so lends itself to everyone being in a room together. This has been quite hard the last two years. It also doesn’t look to be getting any easier, so we should probably get used to it. Here’s how I’ve been doing it with several teams.
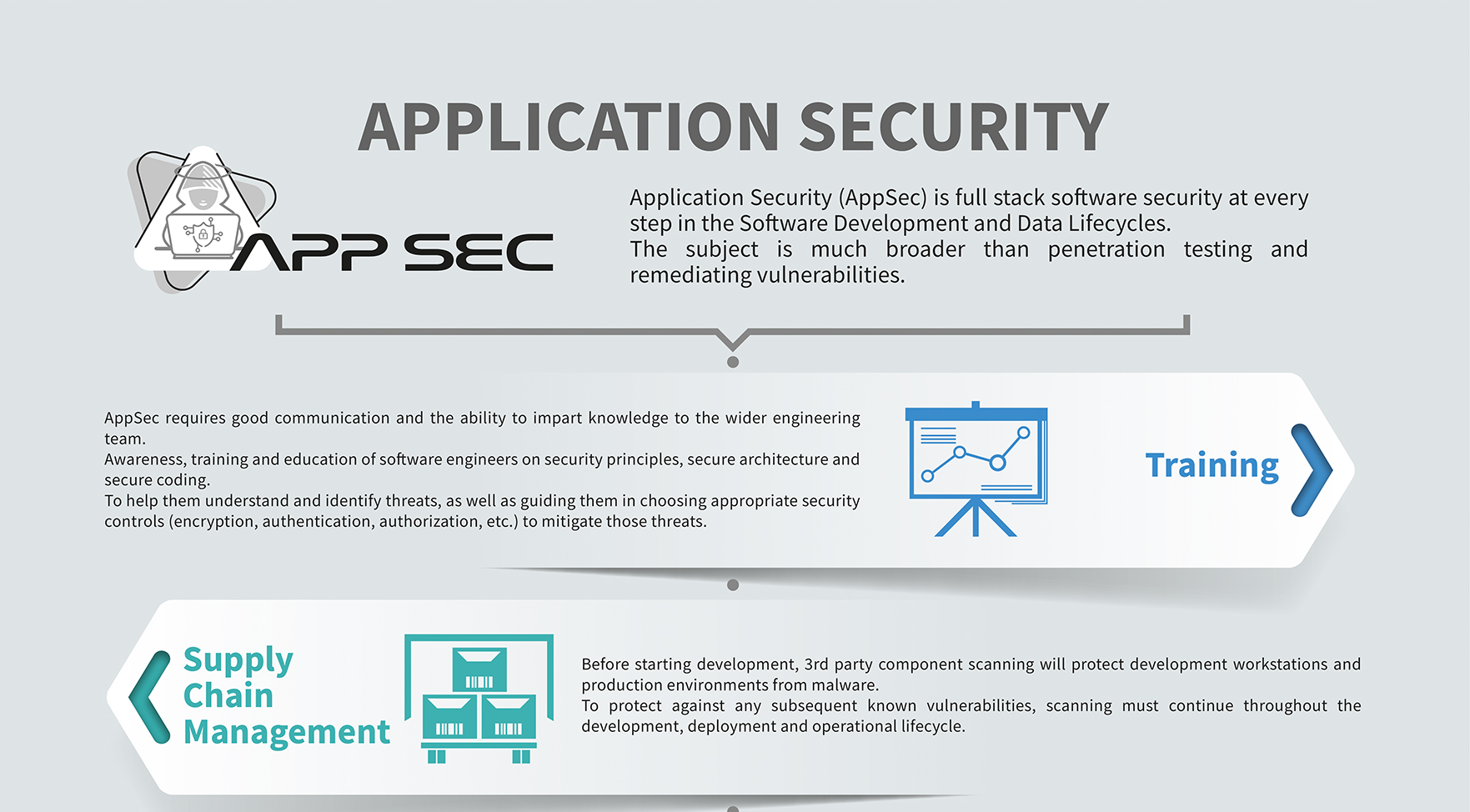
So often organizations believe that Application Security stops at penetration testing and fixing vulnerabilities but it is more than that, penetration testing is the reactive side of things but you also need the proactive aspects of Application Security to reduce the flow.
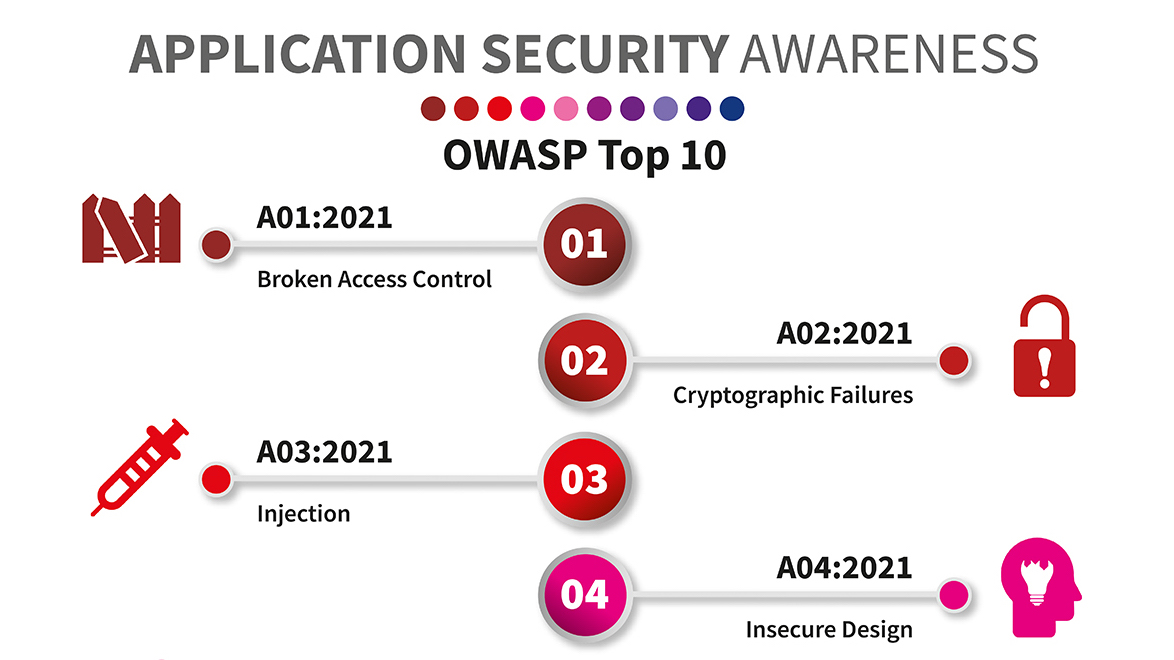
I’ve just launched the first OWASP Application Security Awareness Campaign with 11 Posters of the OWASP Top Ten 2021 project.
Prioritising remediation of vulnerabilities based on effective impact and risk using PageRank.

SAML allows your users to be authenticated and authorized without direct interaction with your web site. It does this by creating a trust relationship between the site and a trusted third party who vouches for the identity of the user. This article explains both how this happens and what the additional benefits are.

What is Kerberos? It is an authentication mechanism...

In this article I am going to outline what SSL is, its building blocks and how it works.

In this article I’m going to talk about why we shouldn’t take security for granted, what practices should be part of our process and how the industry may move to enforce this.

In this first article of a series I’m going to start by explaining a little bit about Public Key encryption which is one of the fundamental building blocks of SSL.

Following on from my previous article about configuring SAML SSO with Tomcat and Picketlink this time I will show you how to do the same thing with JBoss Wildfly.