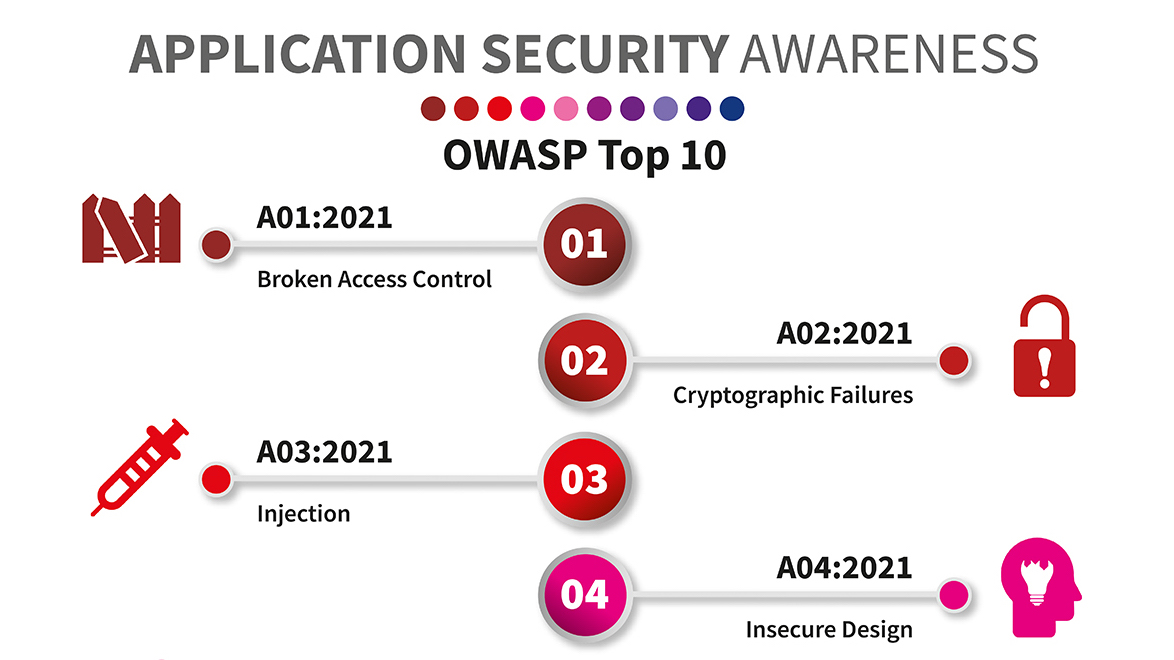
OWASP - Application Security Awareness Campaigns
I’ve just launched the first OWASP Application Security Awareness Campaign with 11 Posters of the OWASP Top Ten 2021 project.

I’ve just launched the first OWASP Application Security Awareness Campaign with 11 Posters of the OWASP Top Ten 2021 project.
Prioritising remediation of vulnerabilities based on effective impact and risk using PageRank.

This is just a collection of notes I’ve made over a period of time to remind me of certain commands or syntax. I will continue adding to this over time. I’m also going to add my Natural Language Processing notes and Machine Learning Notes in a couple of other articles.

SAML allows your users to be authenticated and authorized without direct interaction with your web site. It does this by creating a trust relationship between the site and a trusted third party who vouches for the identity of the user. This article explains both how this happens and what the additional benefits are.

What is Kerberos? It is an authentication mechanism...

What are digital signatures and what do they tell us, what information do they hold? All this and more are explained in this article.

In this article I am going to outline what SSL is, its building blocks and how it works.

In this article I’m going to talk about why we shouldn’t take security for granted, what practices should be part of our process and how the industry may move to enforce this.