Kicking Off Security Maturity
Building an AppSec Program: A Collaborative Approach Are...

Brett is a Seasoned Application Security Engineer and Thought Leader with a Proven Track Record in Software Engineering and Security Best Practices.
Brett has over 10 years of application security experience and 25 years in software engineering. He holds (ISC)² certifications including CISSP, CSSLP, and CCSP. As the author of Threat Modeling Gameplay with EoP and the project lead for the OWASP Application Security Awareness Campaigns, Brett actively contributes to the security community. He also maintains the Ostering.com blog, where he shares insights on security practices.
Brett has successfully collaborated with teams to define security best practices and integrate security by design into their software development lifecycle (SDLC). His training initiatives in threat modeling have led to significant improvements in design quality and security awareness within organizations.
In his spare time, Brett enjoys sports, gardening, cooking, and photography. He is fluent in both English and Italian and holds dual citizenship.
Key Skills: Secure by Design, Privacy by Design, Threat Modeling (STRIDE, EoP, Privacy, LinddunGO, Plot4AI), Secure Coding, Vulnerability Management, and more.
Brett welcomes connections and opportunities to collaborate on innovative security solutions.

Building an AppSec Program: A Collaborative Approach Are...

AI-Generated Code: Productivity Gains, Security Pains, and the...

There are lots of ways we can optimise what we do, through a data driven approach, but we need to be careful and use critical and creative thinking.

Why are so many people just diving, straight into the code? A minimum of requirements and design? Perhaps a threat Model?
We need to fix the culture, from top to bottom in the software engineering industry. Here are just some of the issues as I see them and what we should be doing about them.

Coming soon to a bookshelf near you, Threat Modeling Gameplay with EoP: A reference manual for spotting threats in software architecture

Some interesting security and creativity games plus a few more
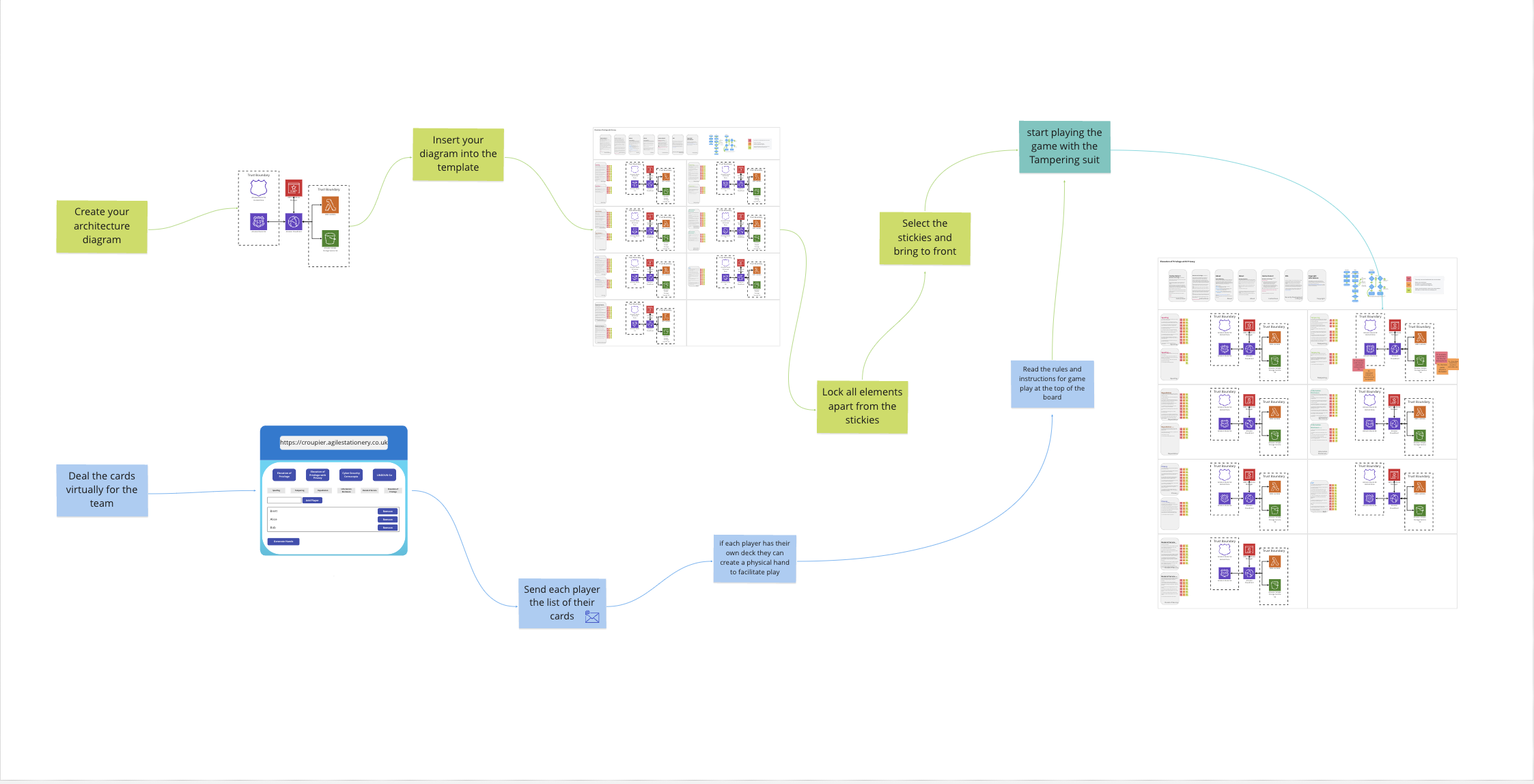
Threat modeling with teams is a process that requires visuals, interaction between team members and discussion and so lends itself to everyone being in a room together. This has been quite hard the last two years. It also doesn’t look to be getting any easier, so we should probably get used to it. Here’s how I’ve been doing it with several teams.
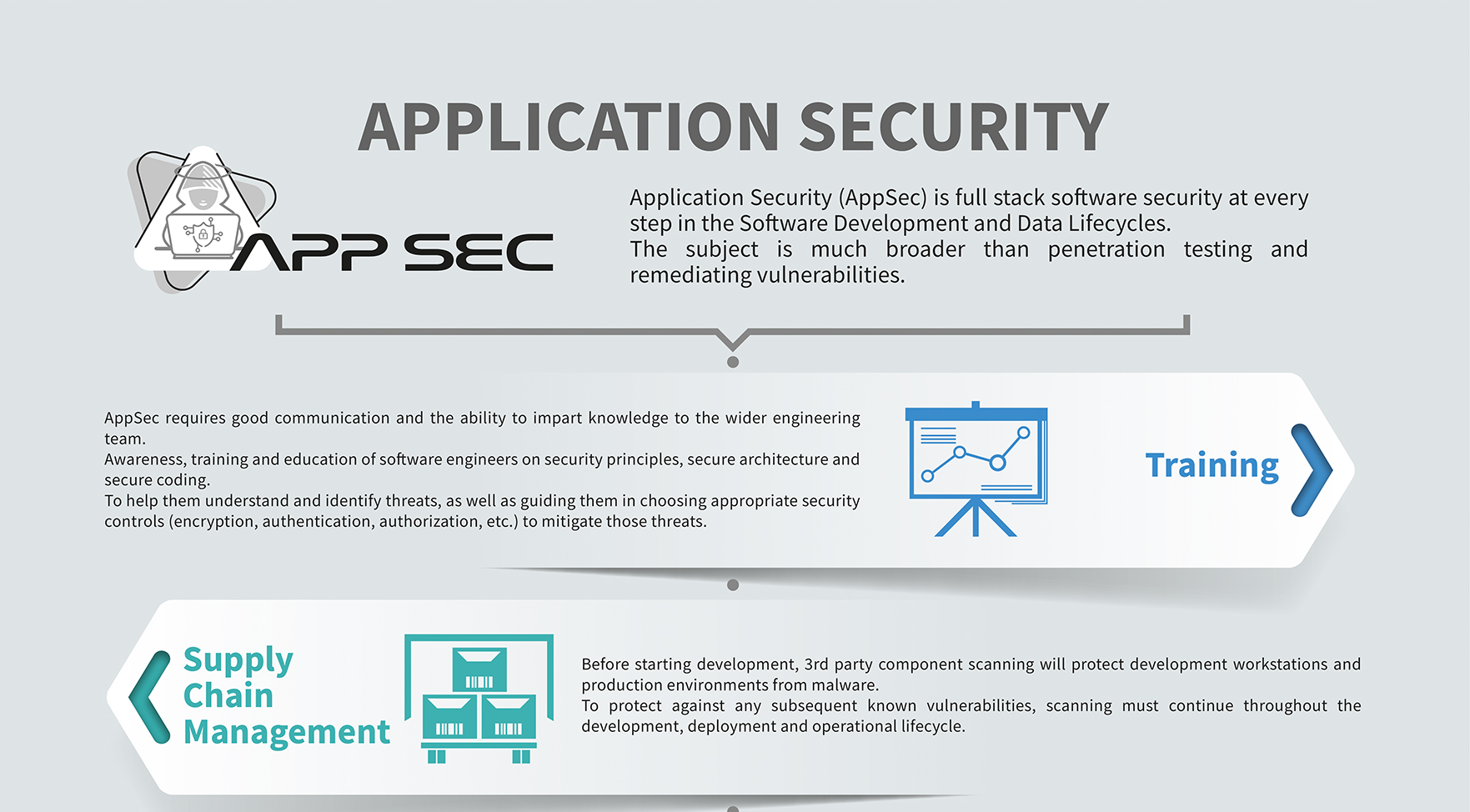
So often organizations believe that Application Security stops at penetration testing and fixing vulnerabilities but it is more than that, penetration testing is the reactive side of things but you also need the proactive aspects of Application Security to reduce the flow.
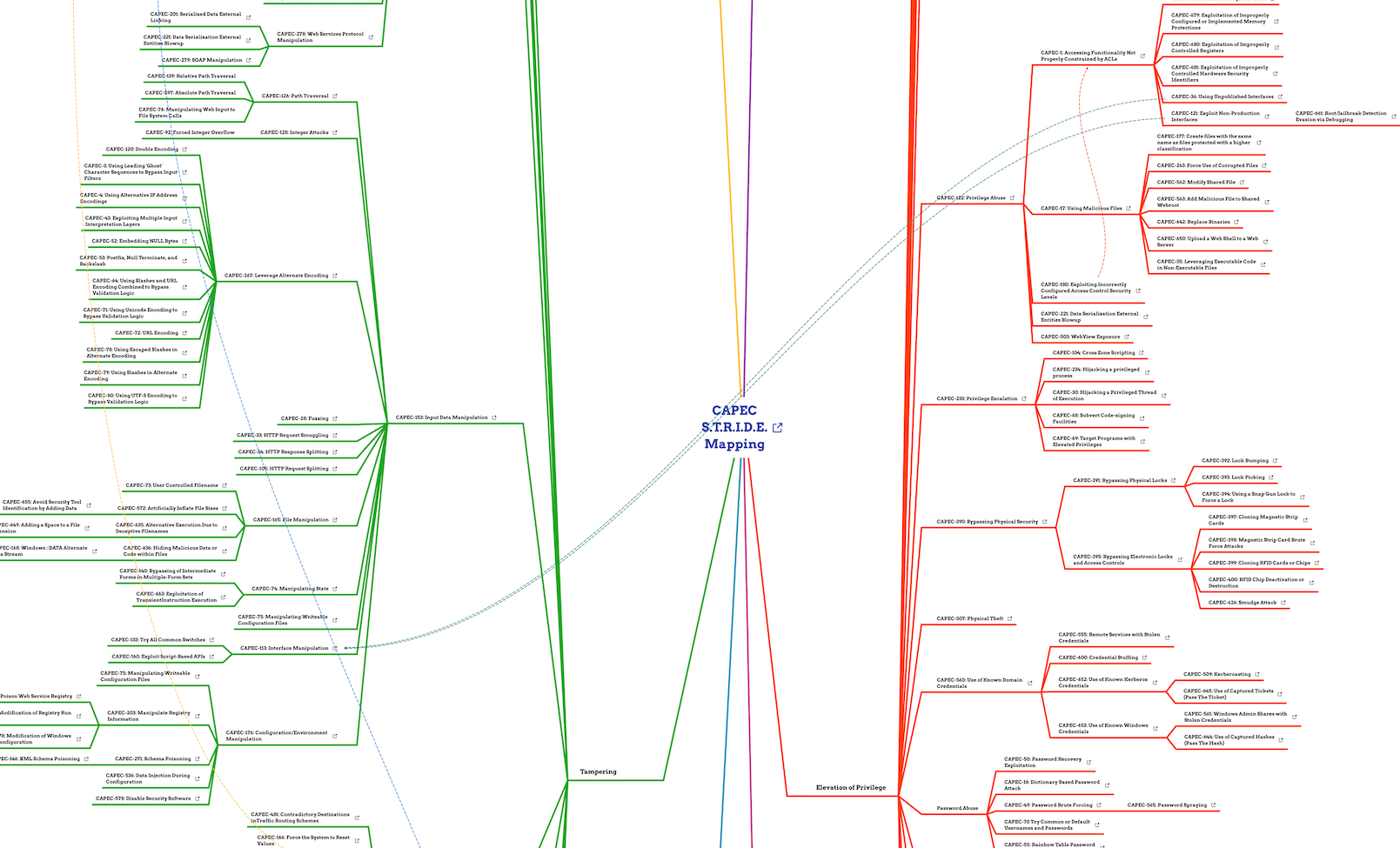
Mapping between the Common Attack Pattern Enumeration and Classification (CAPEC) from Mitre and the S.T.R.I.D.E. Categories used in Threat Modeling.
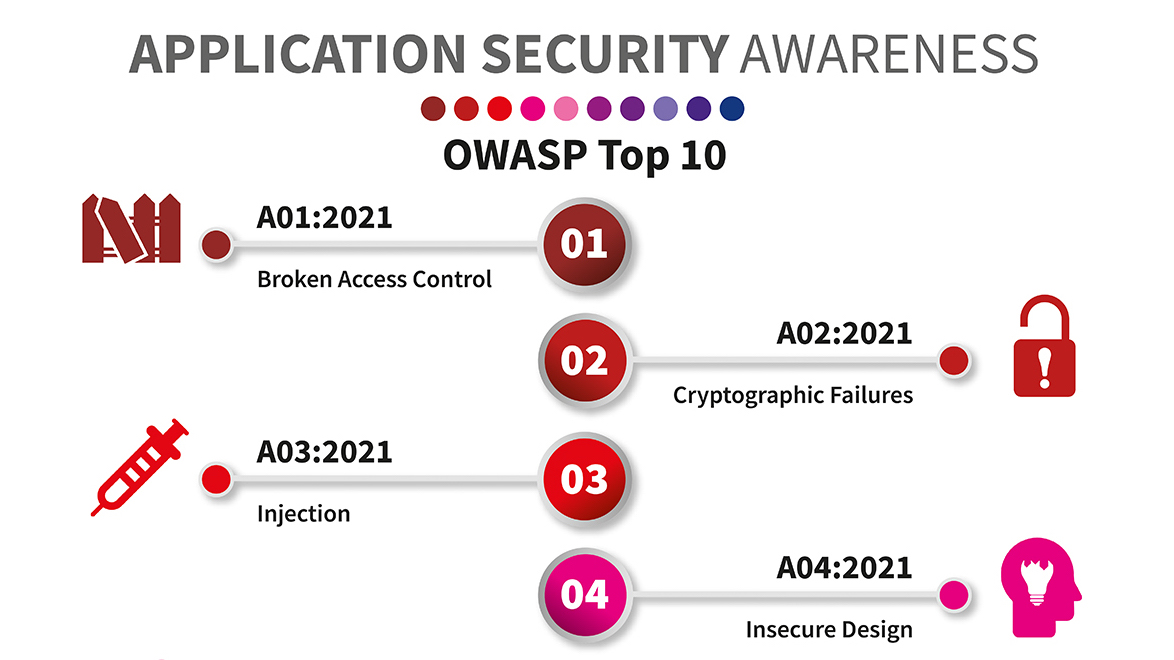
I’ve just launched the first OWASP Application Security Awareness Campaign with 11 Posters of the OWASP Top Ten 2021 project.
Prioritising remediation of vulnerabilities based on effective impact and risk using PageRank.