Kicking Off Security Maturity
Building an AppSec Program: A Collaborative Approach
- Are you looking to kickstart an Application Security (AppSec) program?
- Do you want to assess your organization’s security maturity?
- Or perhaps you’re aiming to cultivate a stronger security culture?
If any of these resonate with you, this method might be just what you need, especially if you’re managing multiple teams. It’s an approach I’ve been eager to present at a conference, and I’m excited to share it with you.
The Current State of AppSec Maturity Assessments
Typically, assessing security maturity involves interviewing teams one by one. While this approach works, it’s often slow and inefficient. Many maturity models rely on specific, task-oriented questions like:
- “Are you performing threat modeling for your designs?”
- “Does your team conduct SAST scanning?”
These questions can unintentionally condition or influence responses. Team members may feel pressured to report that they’re meeting these expectations, even if they’re not. This can lead to awkwardness and inaccuracies.
At this stage, you’re simply gathering information. Later, the goal is to help teams build a roadmap toward better security practices. This often gets push back, but what if there’s a more engaging, collaborative way to approach this process? Let’s explore an alternative method.
A New Approach to AppSec Maturity
Step 1: Information Gathering with Post-Its
Instead of conducting structured interviews, invite teams to map out their processes using post-it notes on a timeline. Avoid prompts to eliminate bias. This freeform approach allows teams to accurately represent what they do. Tasks performed in parallel can be stacked for clarity. Here’s an example of what this might look like:
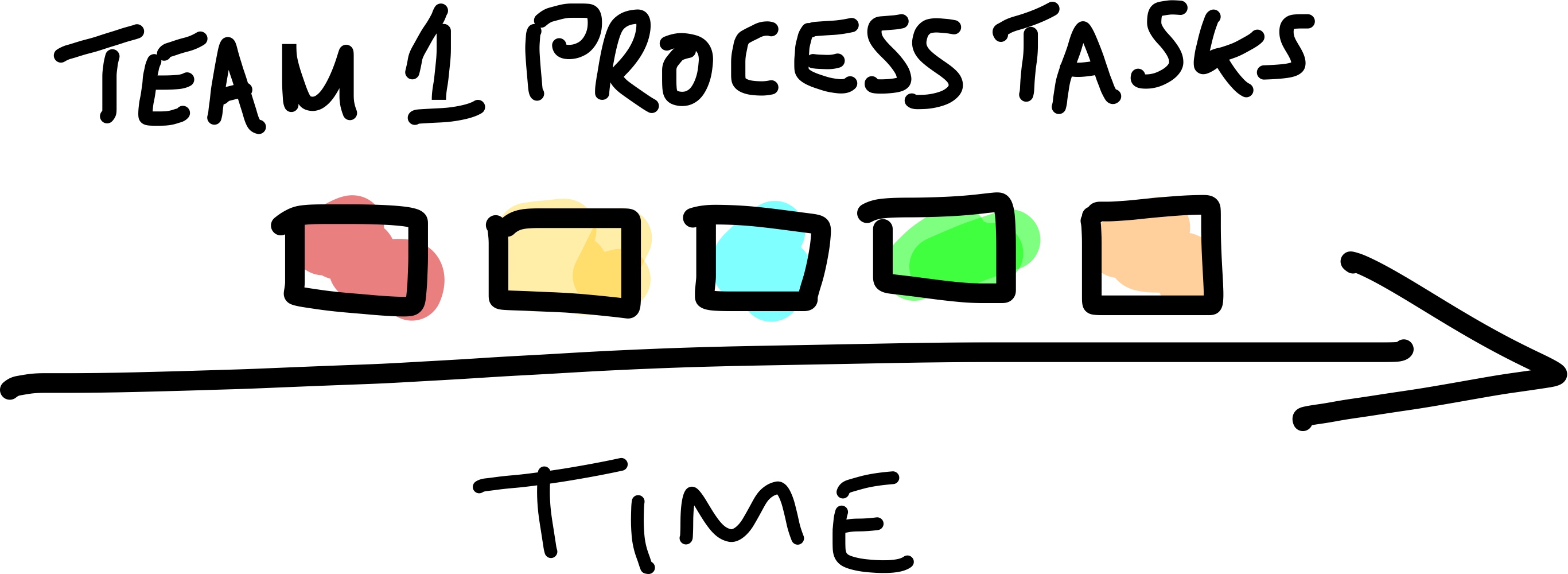
Note: When I talk about getting teams participate, this may only require a representative of the team with sufficient knowledge of their process and sufficient seniority to be able to initiate change.
Step 2: Aggregating Processes
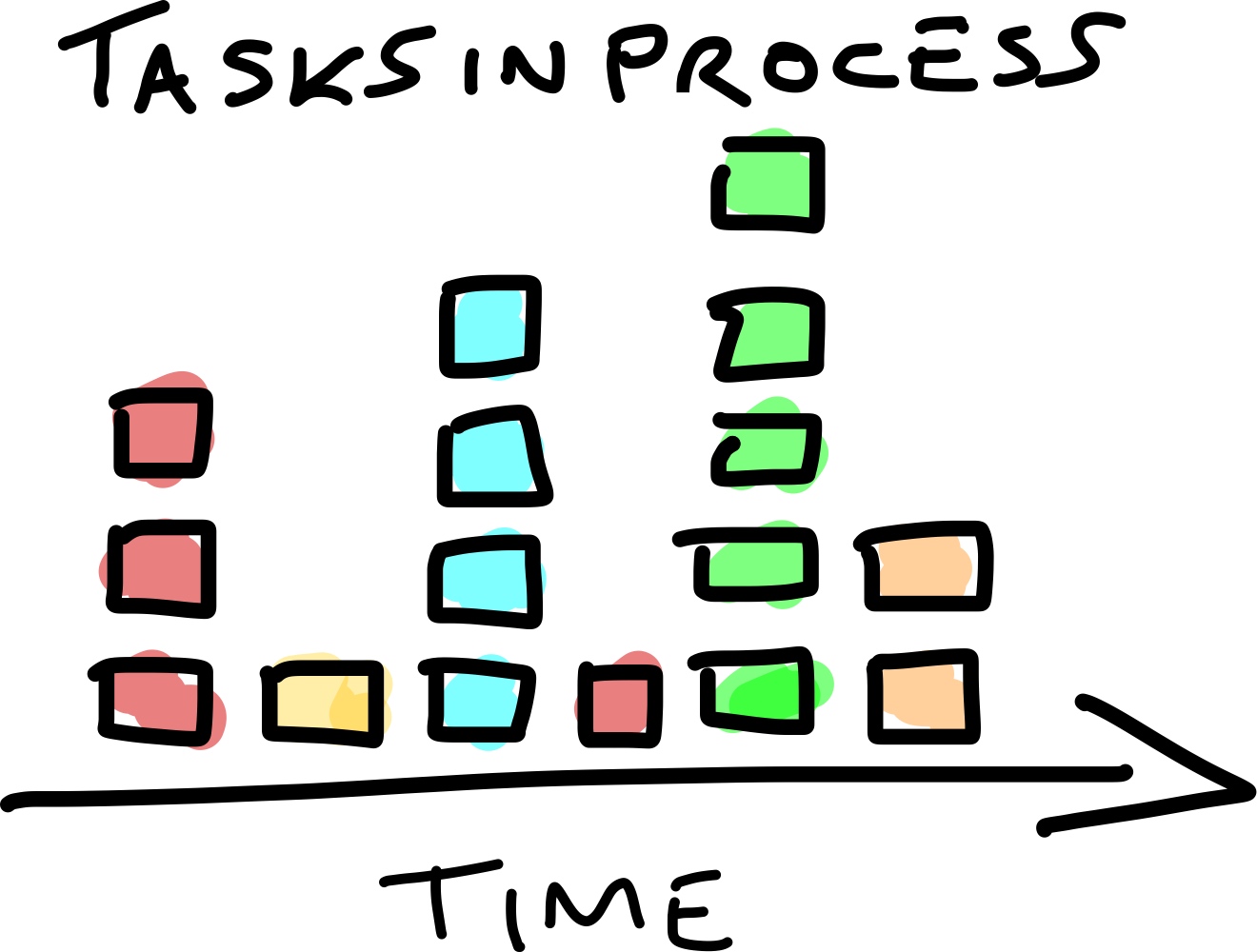
Once all teams have documented their workflows, combine them into a unified timeline. Group similar tasks together while maintaining the sequence. This aggregated view provides a bird’s-eye perspective of all processes, like this:
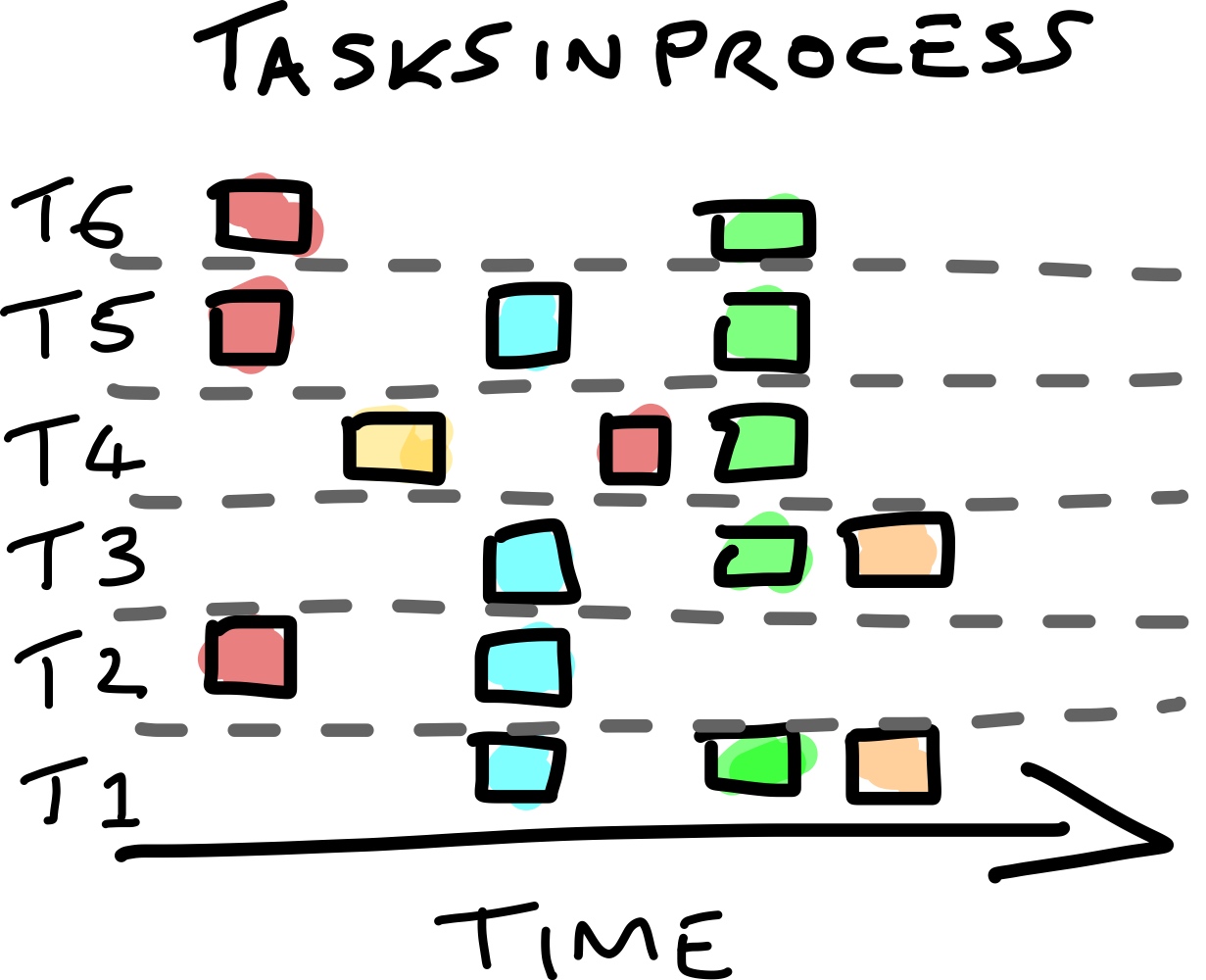
Step 3: Analyzing Patterns
Now, patterns and gaps instantly emerge. For instance:
- Some tasks, like the red, blue, and green ones, are widely adopted across teams.
- Others, like the yellow and orange tasks, are rarely performed. Are these tasks early-stage innovations, or have they been abandoned?
- Additionally, one team performs the red task at a different point in the process. Why? Is it more effective there?
This analysis paves the way for meaningful discussions and improvements.
Step 4: Facilitating Consensus and Collaboration
Next, bring the teams together to share their workflows. As the facilitator, your role is to guide the conversation, introduce industry best practices, and encourage open, blame-free discussions. Start by presenting the aggregated timeline, without team labels, to foster psychological safety.
Encourage teams to explain the benefits of widely adopted tasks. This sparks curiosity among others, prompting them to ask, “Why aren’t we doing that?” This technique, known as Social Proofing, helps shift the dynamic from “push” to “pull.” Instead of enforcing changes, teams will seek out your guidance.
Be objective about consensus though because there may be better solutions you can share with the teams.
Addressing Specific Scenarios
Early Adopters as Champions
Early adopters can share their experiences, highlighting the benefits and challenges of tasks they’ve embraced. Their insights can inspire others to try these practices.
Abandoned Tasks
If some tasks have been dropped, explore why. Was it due to inefficiency, a lack of resources, or an unresolved challenge? Collaborate with teams to identify solutions or alternatives.
Task Timing
If a task is performed at different stages by different teams, discuss the reasons behind the variations. This can lead to valuable insights about the optimal timing for specific activities.
Step 5: Introducing Missing Practices
Finally, identify gaps in the workflows. Add suggestions for missing tasks to the timeline and ask teams to discuss where they might fit best. This encourages teams to consider the value of new practices in their own context.
The Benefits of This Approach
By using this collaborative method, you:
- Gain a clear understanding of what teams are doing and why.
- Foster trust and transparency between teams and AppSec.
- Enable teams to learn from one another, leveraging the trust they’ve already built.
- Empower teams to take ownership of their security maturity journey.
Instead of pushing for change, this approach encourages teams to ask for your help in integrating new tasks into their workflows.
Final Thoughts
This method is a proposal, and while it lacks empirical data, it’s designed to provoke discussion and experimentation. It’s not a replacement for frameworks like OWASP SAMM or BSIMM but rather a complementary way to kickstart a security improvement program.
It is not meant as a method of measurement for reporting, it is mean’t to:
- to drive change in security culture from push to pull
- to aid the AppSec team in understanding the current security posture
- to build awareness in the development teams
- to support and guide teams in creating their own roadmap
- to build trust between development teams and AppSec
If it is successful in any of these then it has done it’s job, if it manages on multiple fronts the it’s a bonus.
Facilitation requires experience in AppSec and leading group discussions. The process works equally well with remote teams using tools like Miro or Mural.
If you try this approach or want to discuss it further, feel free to connect with me on LinkedIn. Let’s collaborate to shape the future of AppSec culture.